1. Metasploit – Penetration Testing Software:
It provides data on the vulnerabilities in the security system and performs penetration tests. Metasploit evades leading anti-virus solutions 90% of the time and enables you to completely take over a machine you have compromised from over 200 modules.
As a penetration tester, it pin points the vulnerabilities with Nexpose closed–loop integration using Top Remediation reports. Using the open source Metasploit framework, users can build their own tools and take the best out of this multi-purpose hacking tool.
2. Acunetix Web:
Acunetix is a web vulnerability scanner (WVS) that scans and finds out the flaws in a website that could prove fatal. By using Acunetix Web Vulnerability Scanner you can perform a full web scan from your computer in windows.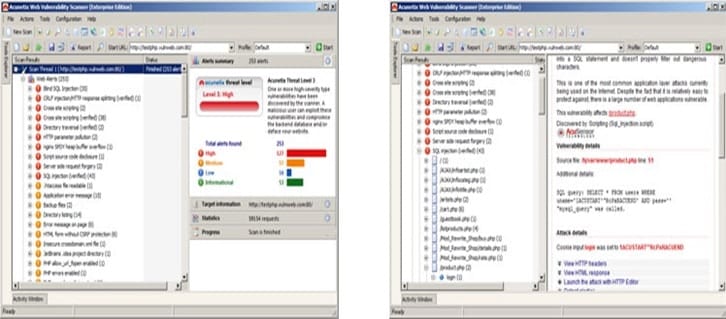
This is the fast and easy which scans WordPress websites from more than 1200 vulnerabilities in WordPress.
3. Nmap (Network Mapper):
Nmap (Network Mapper) is a port scanner tool. It is used to discover hosts and services on a computer network. It is capable of Host Discovery, Port Scanning, Service Name and Version Detection, OS Detection.
It is capable for tasks such as network inventory, managing service upgrade schedules, and monitoring host or service uptime.
4. oclHashcat:
You might be aware of the free password cracking tool Hashcat. While Hashcat is a CPU-based password cracking tool, oclHashcat is the advanced version that uses the power of your GPU. oclHashcat is the world’s fastest password cracking tool with world’s first and only GPGPU based engine.
For using this tool, NVIDIA users require ForceWare 346.59 or later and AMD users require Catalyst 15.7 or later. It is released as free software and the versions available for Linux, OS X, and Windows and can come in CPU-based or GPU-based variants.
5. Wireshark:
Wireshark is the world’s foremost and widely-used network protocol analyzer.
Wireshark has rich features such as Deep inspection of hundreds of protocols, with more being added all the time, Multi-platform i.e; Runs on Windows, Linux, MacOS, Solaris, FreeBSD, NetBSD, and many others. It monitors every single byte of the data that is transferred via the network system.
